折腾:
【已解决】小程序中如何让api服务器满足要求:已备案的带域名的https
期间,需要继续去弄给
的端口转发后,再去添加https的支持。
另外,刚发现:
【已解决】域名加上https支持后html的js中访问api出错:The page at was loaded over HTTPS, but requested an insecure XMLHttpRequest endpoint
所以也必须实现上述需求。
目前的情况是:
上已经加了https的ssl证书,和强制80的http去301跳转到443的https
server {
listen 80 default_server;
return 301 https://$host$request_uri;
}
server
{
listen 443 ssl;
server_name xxx www.xxx;
...
}对于dev.xxx,本身阿里云的DNS中已配置了二级域名:
A dev 默认 xxx
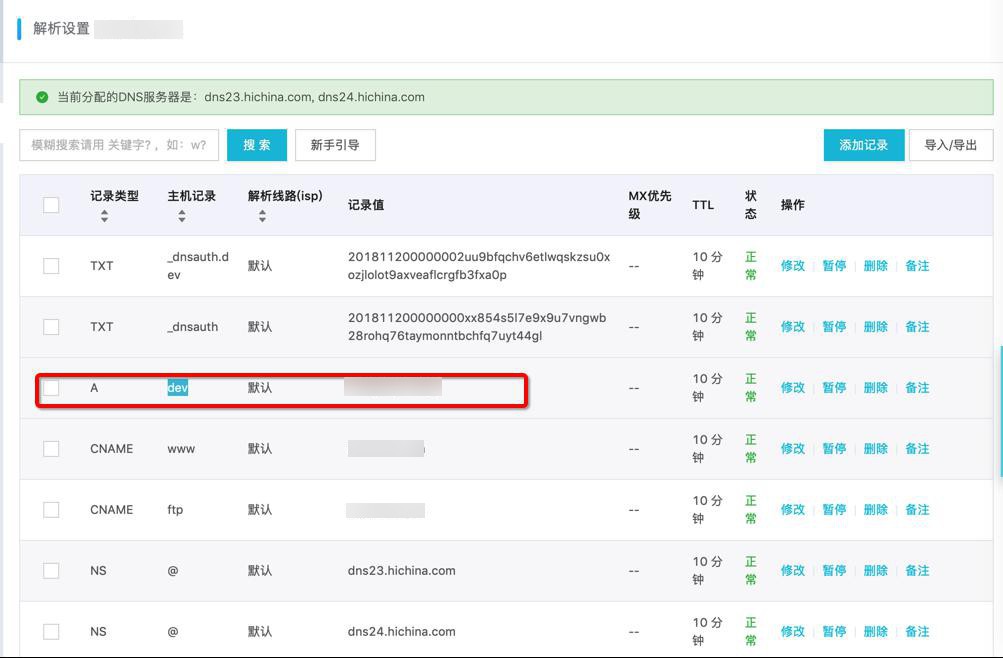
而dev服务器中,也已经设置好了端口转发到33800端口:
conf.d/dev.xxx.conf
server
{
listen 80;
server_name dev.xxx;
...
location /storybook/
{
proxy_pass http://xxx:33800/;
}
}现在需要:
确保访问https的:
https://dev.xxx/storybook/xxx
可以跳转到
https://xxx:33800/xxx
之前访问:
会打开对应的dev服务器的html首页
现在是:
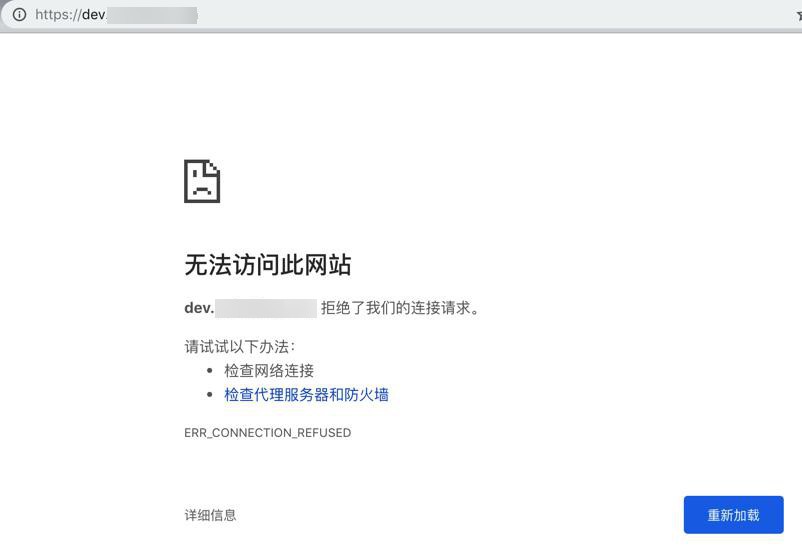
无法访问此网站
拒绝了我们的连接请求
-》看起来应该也是 端口没有打开?
先不管,先去看看:
还是可以打开的:
现在感觉还是有点奇怪:
根据之前的别人的解释,觉得也是对的:
访问:
http://dev.xxx
首先应该是DNS去把
dev.xxx
解析到
xxx
才对啊
而不是此处的:
www.xxx的nginx配置的:
http用301跳转到https,变成了:
和
server {
listen 80 default_server;
server_name xxx www.xxx;
return 301 https://$host$request_uri;
}
server
{
# listen 80;
listen 443 ssl;
server_name xxx www.xxx;
# server_name www.xxx;
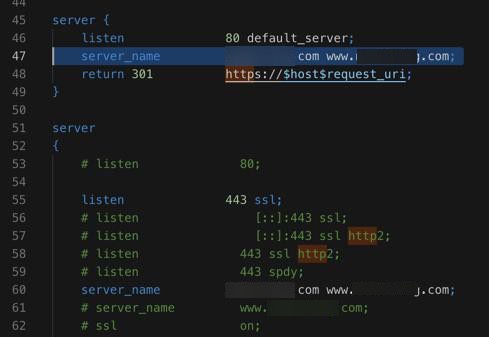
结果问题依旧。
先去想办法找找:
此处的
http://dev.xxx
跳转到
https://dev.xxx
到底是哪个服务器收到了log了。
通过:
tail /www/wwwlogs/www.xxx_https.log tail /www/wwwlogs/www.xxx_https_error.log tail /www/wwwlogs/access.log tail /www/wwwlogs/nginx_error.log
确定了:
不是www.xxx的服务器中的log
突然想到:
难道是:
在购买免费的ssl证书的时候:
【已解决】购买阿里云首年免费的https证书:Symantec免费型DV SSL证书
对于dev.xxx,也是采用了,阿里云的万网,然后此处的二级域名解析期间,即:
从dev.xxx,解析到xxx,同时发现已经购买了免费的ssl证书,所以自动跳转到
https://dev.xxx了?
总之很奇怪。
反正确定了是dev服务器的事情,所以去看dev服务器中的nginx的配置和log
结果dev中也没有对应log:
tail /var/log/nginx/dev.xxx/access.log tail /var/log/nginx/dev.xxx/error.log
才想起来:
应该还是443端口被禁止访问的结果:
(虽然之前已经用阿里云的安全组加了443端口了:
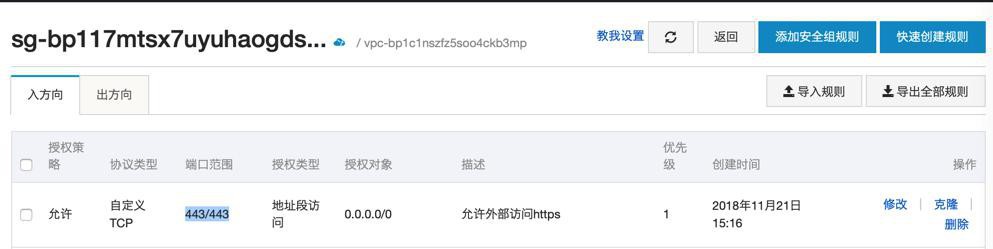
但是没用)
还是去参考之前的:
【已解决】CentOS 7中如何通过firewalld去添加https的443端口
去添加支持https的443端口:
结果是没有运行:
[root@xxx-general-01 ~]# firewall-cmd --zone=public --list-all FirewallD is not running [root@xxx-general-01 ~]# firewall-cmd --state not running [root@xxx-general-01 ~]# service firewalld status Redirecting to /bin/systemctl status firewalld.service ● firewalld.service - firewalld - dynamic firewall daemon Loaded: loaded (/usr/lib/systemd/system/firewalld.service; disabled; vendor preset: enabled) Active: inactive (dead) Docs: man:firewalld(1)
那去看看iptables:
[root@xxx-general-01 ~]# iptables -L --line-number Chain INPUT (policy ACCEPT) num target prot opt source destination Chain FORWARD (policy ACCEPT) num target prot opt source destination Chain OUTPUT (policy ACCEPT) num target prot opt source destination
好像也没有开启?
那暂时先不去开启防火墙,先去给dev的nginx加上443的https端口监听,看看能否收到log。
不过此处虽然已经知道了:
无法访问:
但也还是继续去试试:
server {
listen 80 default_server;
server_name dev.xxx;
return 301 https://$host$request_uri;
}
server {
listen 443 ssl;
server_name dev.xxx;
access_log /var/log/nginx/dev.xxx/access_https.log;
error_log /var/log/nginx/dev.xxx/error_https.log;
### Https Related Config
keepalive_timeout 70; # 设置长连接
ssl_certificate /usr/share/nginx/cert/dev.xxx_aliyun_symantec_free_ov_ssl.crt; # 证书文件
ssl_certificate_key /usr/share/nginx/cert/dev.xxx_aliyun_symantec_free_ov_ssl.key; # 私钥文件
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!MD5;
# ssl_session_timeout 10m; # 配置会话超时时间
# ssl_session_cache shared:SSL:10m; # 配置共享会话缓存大小,视站点访问情况设定
# ssl_prefer_server_ciphers on; #优先采取服务器算法
# # 如果是全站 HTTPS 并且不考虑 HTTP 的话,可以加入 HSTS(HTTP Strict Transport Security) ,使用 HSTS 策略强制浏览器使用 HTTPS 连接
# add_header Strict-Transport-Security "max-age=31536000; includeSubDomains;preload" always;
# add_header X-Frame-Options DENY; #减少点击劫持
# add_header X-Content-Type-Options nosniff; #禁止服务器自动解析资源类型
# add_header X-Xss-Protection 1; #防XSS攻击
proxy_set_header HOST $host;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_http_version 1.1;
location /storybook/
{
proxy_pass https://xxx:33800/;
}
}至少看看能否收到log
结果测试出错:
}[root@xxx-general-01 conf.d]# service nginx reload Redirecting to /bin/systemctl reload nginx.service [root@xxx-general-01 conf.d]# nginx -t nginx: [emerg] a duplicate default server for 0.0.0.0:80 in /etc/nginx/nginx.conf:39 nginx: configuration file /etc/nginx/nginx.conf test failed
才注意到之前的:
/nginx.conf
中有:
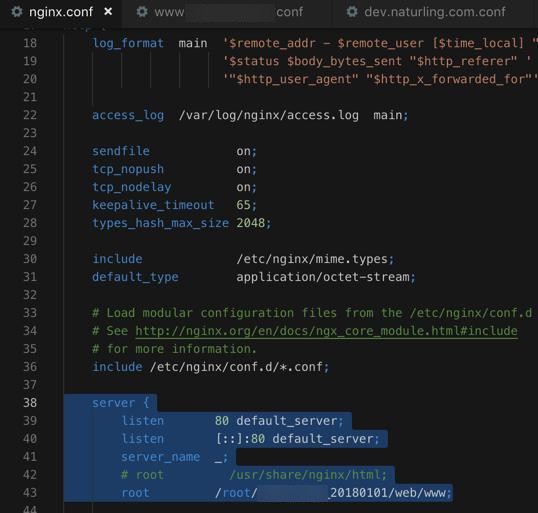
所以暂时去掉自己的80的监听:
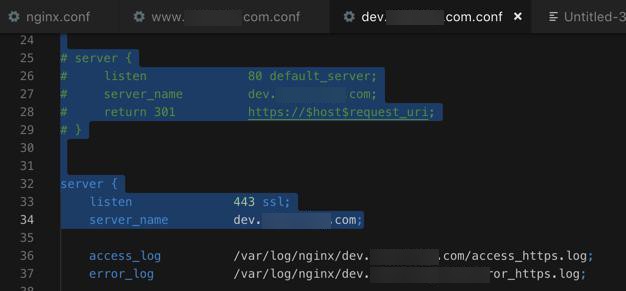
结果:
[root@xxx-general-01 conf.d]# nginx -t nginx: the configuration file /etc/nginx/nginx.conf syntax is ok nginx: configuration file /etc/nginx/nginx.conf test is successful [root@xxx-general-01 conf.d]# service nginx reload Redirecting to /bin/systemctl reload nginx.service [root@xxx-general-01 conf.d]# service nginx status Redirecting to /bin/systemctl status nginx.service ● nginx.service - The nginx HTTP and reverse proxy server Loaded: loaded (/usr/lib/systemd/system/nginx.service; enabled; vendor preset: disabled) Active: active (running) since Mon 2018-11-19 17:10:17 CST; 1 weeks 1 days ago Process: 31657 ExecReload=/bin/kill -s HUP $MAINPID (code=exited, status=0/SUCCESS) Process: 15738 ExecStart=/usr/sbin/nginx (code=exited, status=0/SUCCESS) Process: 15734 ExecStartPre=/usr/sbin/nginx -t (code=exited, status=0/SUCCESS) Process: 15732 ExecStartPre=/usr/bin/rm -f /run/nginx.pid (code=exited, status=0/SUCCESS) Main PID: 15740 (nginx) CGroup: /system.slice/nginx.service ├─15740 nginx: master process /usr/sbin/nginx ├─31659 nginx: worker process ├─31660 nginx: worker process ├─31661 nginx: worker process └─31662 nginx: worker process Nov 19 17:10:17 xxx-general-01 systemd[1]: Starting The nginx HTTP and reverse proxy server... Nov 19 17:10:17 xxx-general-01 nginx[15734]: nginx: the configuration file /etc/nginx/nginx.conf syntax is ok Nov 19 17:10:17 xxx-general-01 nginx[15734]: nginx: configuration file /etc/nginx/nginx.conf test is successful Nov 19 17:10:17 xxx-general-01 systemd[1]: Started The nginx HTTP and reverse proxy server. Nov 28 10:54:44 xxx-general-01 systemd[1]: Reloaded The nginx HTTP and reverse proxy server. Nov 28 11:01:10 xxx-general-01 systemd[1]: Reloaded The nginx HTTP and reverse proxy server.
然后去访问:
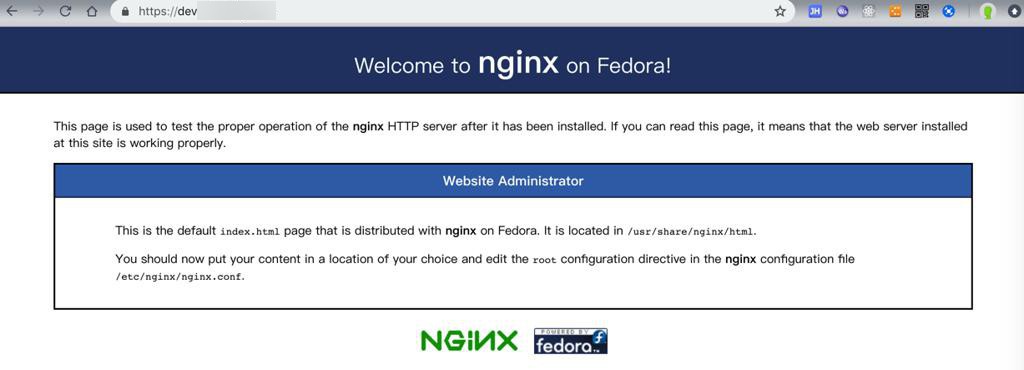
说明443的https生效了。
那再去看看是否转发到端口了:
结果:
502 Bad Gateway nginx/1.12.2
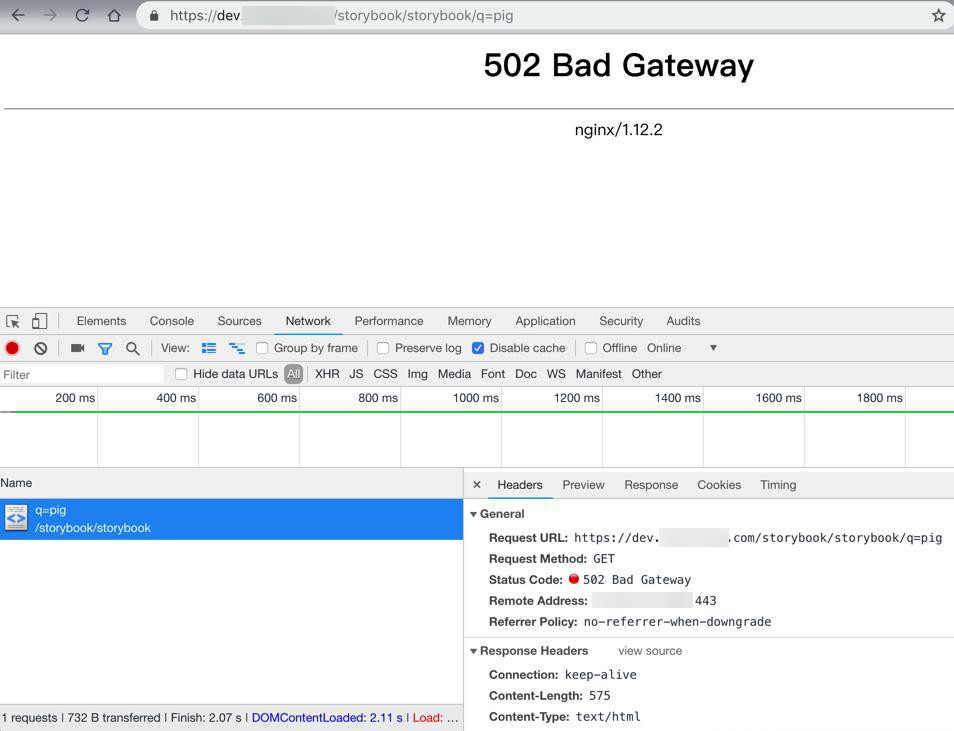
打算去看看log。
不过先去看看:
结果:
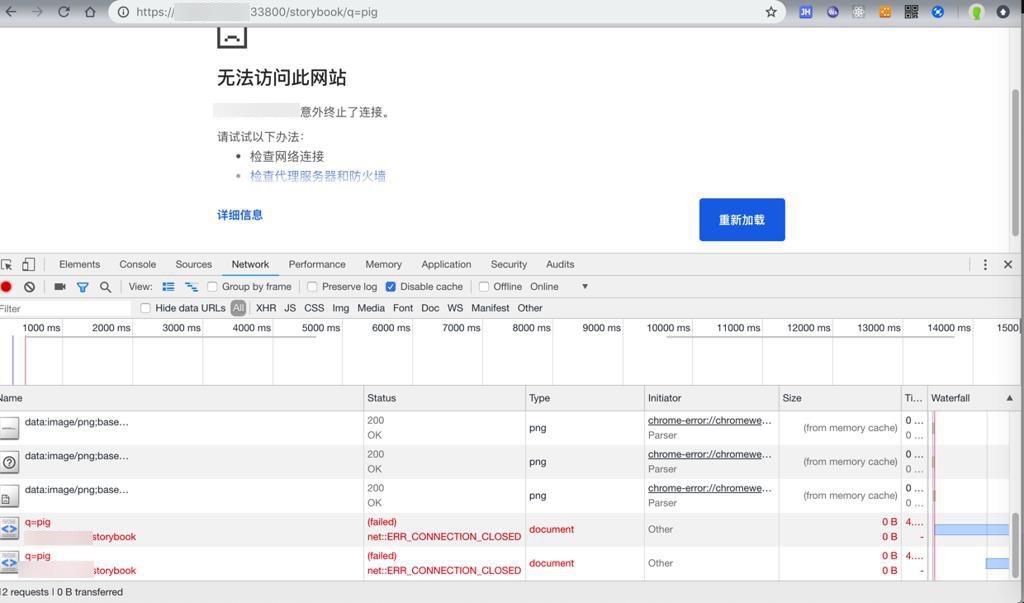
所以还是要去防火墙方面,设置允许33800端口的入方向的访问
不过之前阿里云安全组中已加过了33800的端口入方向了。
抽空再去看看防火墙中的设置。
此处,先去试试:
location /storybook/
{
# proxy_pass https://xxx:33800/;
proxy_pass https://127.0.0.1:33800/;
}看看效果:问题依旧。
nginx https redirect port
参考这个做法去加上额外的listen 33800:
server {
listen 443 ssl;
listen [::]:443 ssl;
server_name dev.xxx;
ssl_certificate /usr/share/nginx/cert/dev.xxx_aliyun_symantec_free_ov_ssl.crt; # 证书文件
ssl_certificate_key /usr/share/nginx/cert/dev.xxx_aliyun_symantec_free_ov_ssl.key; # 私钥文件
# Redirect the browser to our port 9443 config
return 301 $scheme://dev.xxx:33800$request_uri;
}
server {
listen 33800 ssl;
listen [::]:33800 ssl;
server_name dev.xxx;
access_log /var/log/nginx/dev.xxx/access_https.log;
error_log /var/log/nginx/dev.xxx/error_https.log;
### Https Related Config
ssl_certificate /usr/share/nginx/cert/dev.xxx_aliyun_symantec_free_ov_ssl.crt; # 证书文件
ssl_certificate_key /usr/share/nginx/cert/dev.xxx_aliyun_symantec_free_ov_ssl.key; # 私钥文件
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!MD5;
keepalive_timeout 70; # 设置长连接
# ssl_session_timeout 10m; # 配置会话超时时间
# ssl_session_cache shared:SSL:10m; # 配置共享会话缓存大小,视站点访问情况设定
# ssl_prefer_server_ciphers on; #优先采取服务器算法
# # 如果是全站 HTTPS 并且不考虑 HTTP 的话,可以加入 HSTS(HTTP Strict Transport Security) ,使用 HSTS 策略强制浏览器使用 HTTPS 连接
# add_header Strict-Transport-Security "max-age=31536000; includeSubDomains;preload" always;
# add_header X-Frame-Options DENY; #减少点击劫持
# add_header X-Content-Type-Options nosniff; #禁止服务器自动解析资源类型
# add_header X-Xss-Protection 1; #防XSS攻击
proxy_set_header HOST $host;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_http_version 1.1;
# location /storybook/
# {
# proxy_pass https://xxx:33800/;
# # proxy_pass https://127.0.0.1:33800/;
# }
}结果:
问题依旧,还是:
- https://dev.xxx/storybook/storybook/q=pig
- 502 Bad Gateway
- https://xxx:33800/storybook/q=pig
- 无法访问此网站
参考:
感觉还是需要去加上:
proxy_pass http://127.0.0.1:33800;
去试试:
location /storybook/ {
# proxy_pass https://xxx:33800/;
# proxy_pass https://127.0.0.1:33800/;
proxy_pass http://127.0.0.1:33800/;
}结果:问题依旧。
再去试试:
不用443转特殊端口,直接用443本身,然后443中proxy到http的33800端口:
# server {
# listen 443 ssl;
# listen [::]:443 ssl;
# server_name dev.xxx;
# ssl_certificate /usr/share/nginx/cert/dev.xxx_aliyun_symantec_free_ov_ssl.crt; # 证书文件
# ssl_certificate_key /usr/share/nginx/cert/dev.xxx_aliyun_symantec_free_ov_ssl.key; # 私钥文件
# # Redirect the browser to our port 9443 config
# return 301 $scheme://dev.xxx:33800$request_uri;
# }
server {
# listen 33800 ssl;
# listen [::]:33800 ssl;
listen 443 ssl;
listen [::]:443 ssl;
server_name dev.xxx;
access_log /var/log/nginx/dev.xxx/access_https.log;
error_log /var/log/nginx/dev.xxx/error_https.log;
### Https Related Config
ssl_certificate /usr/share/nginx/cert/dev.xxx_aliyun_symantec_free_ov_ssl.crt; # 证书文件
ssl_certificate_key /usr/share/nginx/cert/dev.xxx_aliyun_symantec_free_ov_ssl.key; # 私钥文件
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!MD5;
keepalive_timeout 70; # 设置长连接
# ssl_session_timeout 10m; # 配置会话超时时间
# ssl_session_cache shared:SSL:10m; # 配置共享会话缓存大小,视站点访问情况设定
# ssl_prefer_server_ciphers on; #优先采取服务器算法
# # 如果是全站 HTTPS 并且不考虑 HTTP 的话,可以加入 HSTS(HTTP Strict Transport Security) ,使用 HSTS 策略强制浏览器使用 HTTPS 连接
# add_header Strict-Transport-Security "max-age=31536000; includeSubDomains;preload" always;
# add_header X-Frame-Options DENY; #减少点击劫持
# add_header X-Content-Type-Options nosniff; #禁止服务器自动解析资源类型
# add_header X-Xss-Protection 1; #防XSS攻击
proxy_set_header HOST $host;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_http_version 1.1;
location /storybook/ {
# proxy_pass https://xxx:33800/;
# proxy_pass https://127.0.0.1:33800/;
proxy_pass http://127.0.0.1:33800/;
}
}结果:
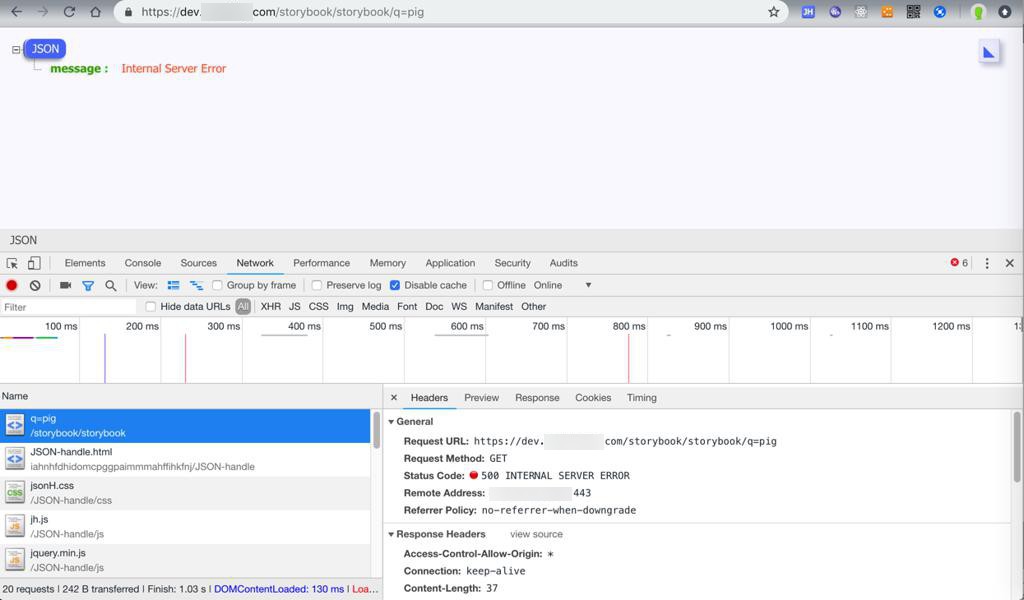
返回:
{
"message": "Internal Server Error"
}
IP+端口:
问题依旧,还是:无法访问此网站
换成:
结果:
问题依旧。
【总结】
最终想要实现:
要访问https://dev.xxx,可以实现跳转到dev服务器的指定端口33800的话,需要去:
到dev服务器中,配置nginx:
- (用ssl证书)支持https
- 且同时支持端口转发
具体配置如下:
server {
listen 443 ssl;
listen [::]:443 ssl;
server_name dev.xxx;
access_log /var/log/nginx/dev.xxx/access_https.log;
error_log /var/log/nginx/dev.xxx/error_https.log;
### Https Related Config
ssl_certificate /usr/share/nginx/cert/dev.xxx_aliyun_symantec_free_ov_ssl.crt; # 证书文件
ssl_certificate_key /usr/share/nginx/cert/dev.xxx_aliyun_symantec_free_ov_ssl.key; # 私钥文件
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!MD5;
...
proxy_set_header HOST $host;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_http_version 1.1;
location /storybook/ {
proxy_pass http://127.0.0.1:33800/;
}
}(而换成)用二级域名去正常访问,传递正确参数的话:
就可以正常返回数据了:
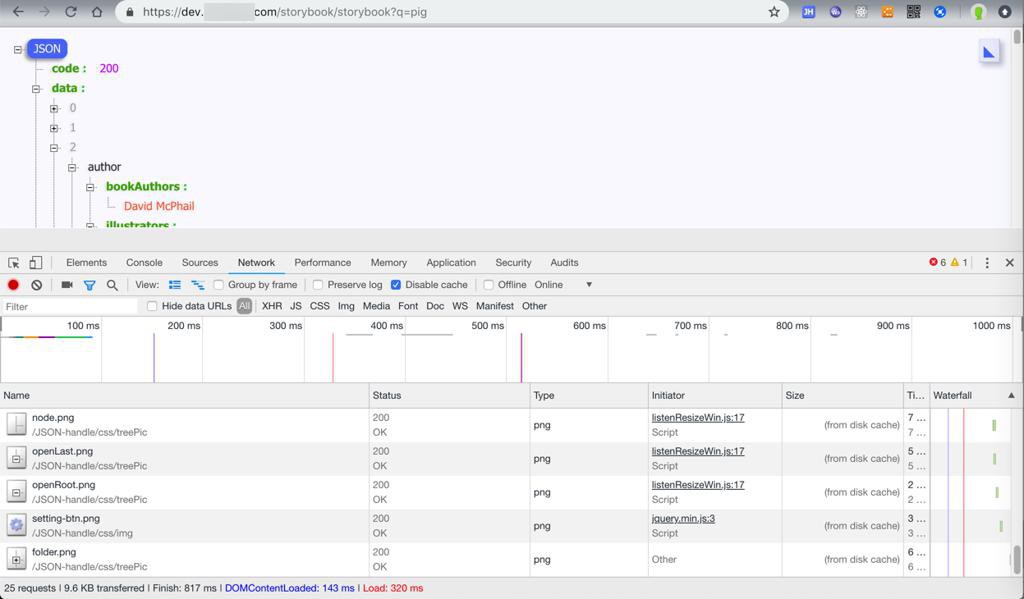
所以目前现象是:
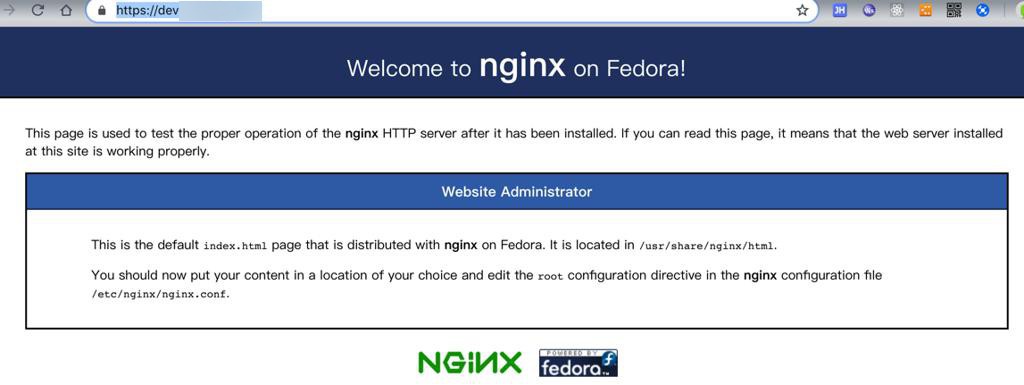
对于dev的二级域名的话:
- https://dev.xxx/
- 正常:返回nginx页面
- https://dev.xxx/storybook/storybook?q=pig
- 正常:返回json数据:
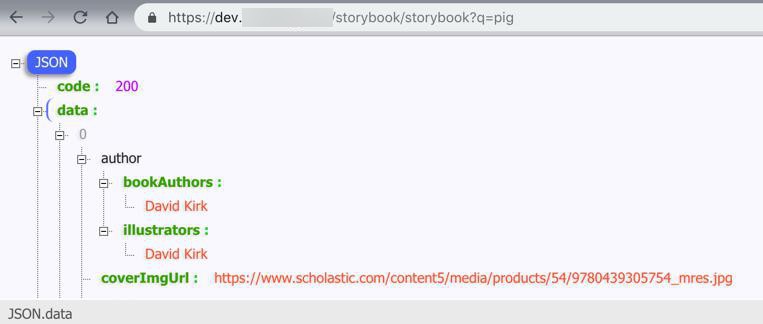
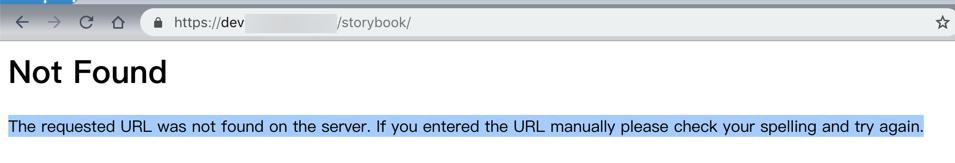
- https://dev.xxx/storybook/
- 正常:没有这个url
- Not Found,The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again.
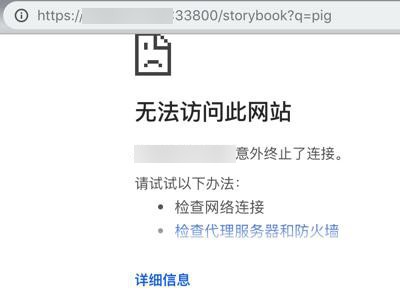
而对于dev服务器的IP访问的话:
- https:https://xxx:33800/storybook?q=pig
- 出错:无法访问此网站
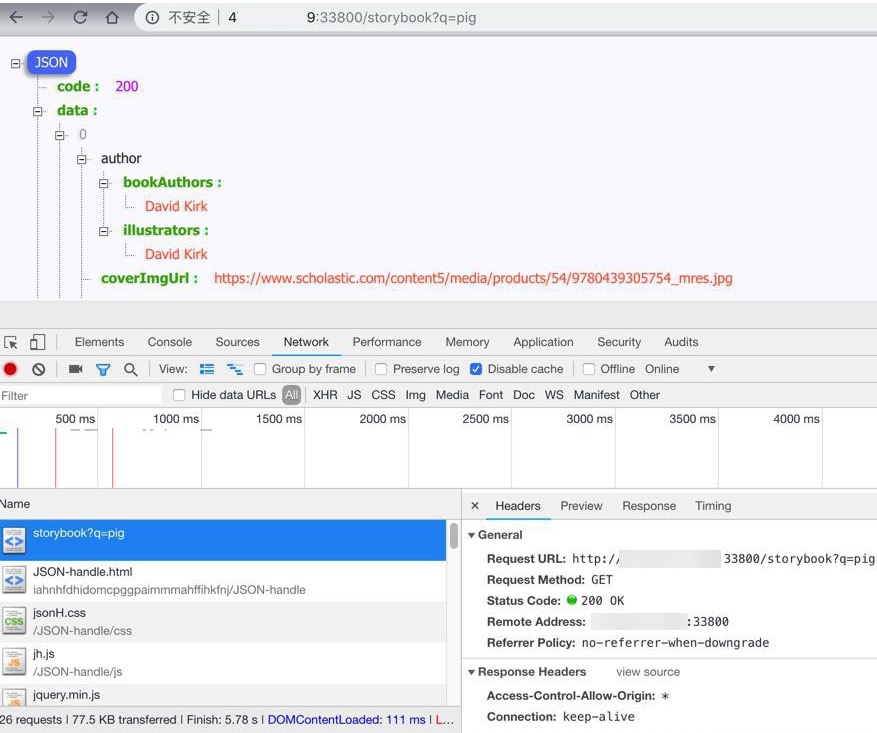
- http:http://xxx:33800/storybook?q=pig
- 正常:可以正常返回json数据
如此,基本上实现了需要的效果:
- 通过dev.xxx的二级域名,正常调用接口是:
- 对于直接用IP+端口访问,则直接用http,不支持https: