折腾:
【未解决】破解安卓应用少儿xxx的源码以便于找到sign签名和auth_token的算法计算逻辑
期间,想办法去导出更加贴近原始代码的,更有可读性的代码。
参考:
去操作。
继续参考
去操作。
先去nox中的Xposed Installer中去激活FDex2
重启Xposed Installer
再去FDex2中的点击要破解的app:少儿xxx
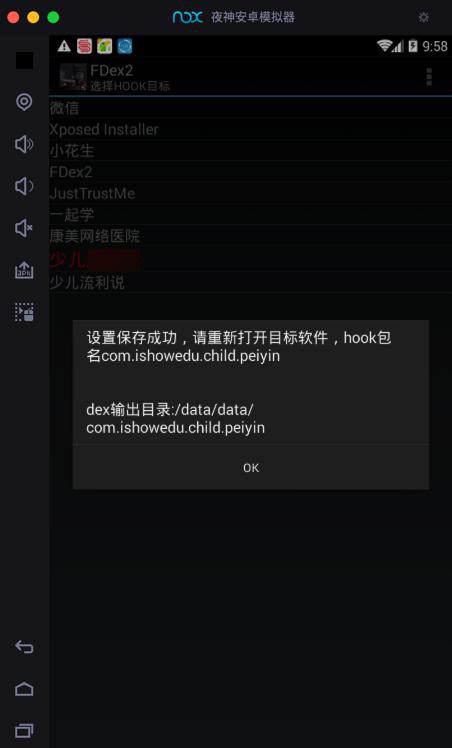
/data/data/com.ishowedu.child.peiyin
再去运行对应的app:
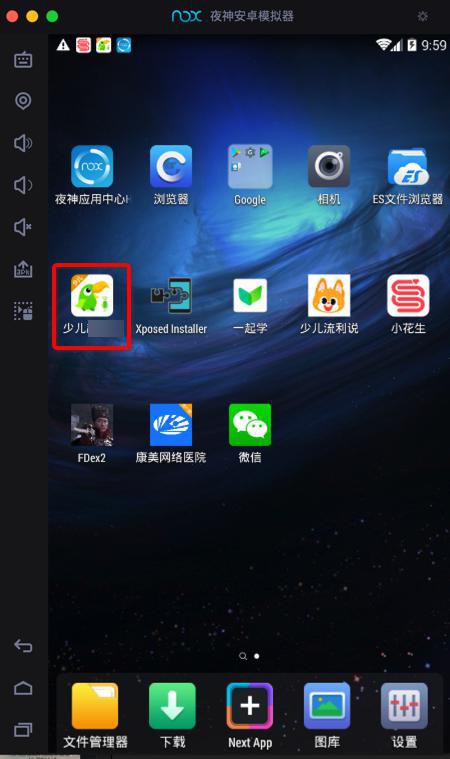
然后再去找到对应目录看看是否导出dex文件
/data/data/com.ishowedu.child.peiyin
是有的
但是没有dex文件
app_dex也是空
重新操作一遍试试
问题依旧。
再去试试,结果直接无法运行
已停止运行
重启nox试试
结果app打开后很慢,无响应,继续等待
不过无所谓,已经得到dex文件了
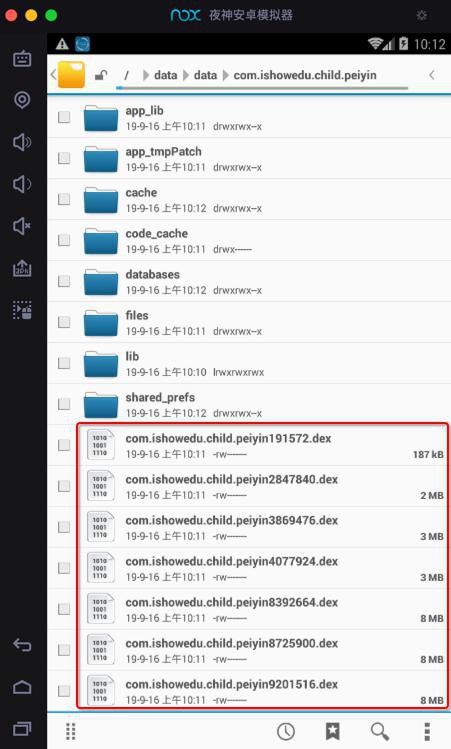
然后去选择,粘贴,导出到mac中
➜ com.ishowedu.child.peiyin pwd /Users/crifan/Library/Application Support/Nox App Player/Nox_share/Other/com.ishowedu.child.peiyin ➜ com.ishowedu.child.peiyin ll total 72888 drwxr-xr-x 3 crifan staff 96B 9 16 10:11 app_bugly drwxr-xr-x 3 crifan staff 96B 9 16 10:12 app_crash drwxr-xr-x 4 crifan staff 128B 9 16 10:11 app_crashrecord drwxr-xr-x 2 crifan staff 64B 9 16 10:11 app_dex drwxr-xr-x 2 crifan staff 64B 9 16 10:11 app_lib drwxr-xr-x 2 crifan staff 64B 9 16 10:11 app_tmpPatch drwxr-xr-x 5 crifan staff 160B 9 16 10:12 cache drwxr-xr-x 3 crifan staff 96B 9 16 10:11 code_cache -rw------- 1 crifan staff 187K 9 16 10:11 com.ishowedu.child.peiyin191572.dex -rw------- 1 crifan staff 2.7M 9 16 10:11 com.ishowedu.child.peiyin2847840.dex -rw------- 1 crifan staff 3.7M 9 16 10:11 com.ishowedu.child.peiyin3869476.dex -rw------- 1 crifan staff 3.9M 9 16 10:11 com.ishowedu.child.peiyin4077924.dex -rw------- 1 crifan staff 8.0M 9 16 10:11 com.ishowedu.child.peiyin8392664.dex -rw------- 1 crifan staff 8.3M 9 16 10:11 com.ishowedu.child.peiyin8725900.dex -rw------- 1 crifan staff 8.8M 9 16 10:11 com.ishowedu.child.peiyin9201516.dex drwxr-xr-x 15 crifan staff 480B 9 16 10:16 databases drwxr-xr-x 9 crifan staff 288B 9 16 10:11 files drwxr-xr-x 25 crifan staff 800B 9 16 10:16 shared_prefs
然后再去后续从dex导出jar,再从jar中导出java源码。
然后对于具体哪个dex才是包含业务逻辑代码的
去用jadx-gui打开各个dex,去预览看看
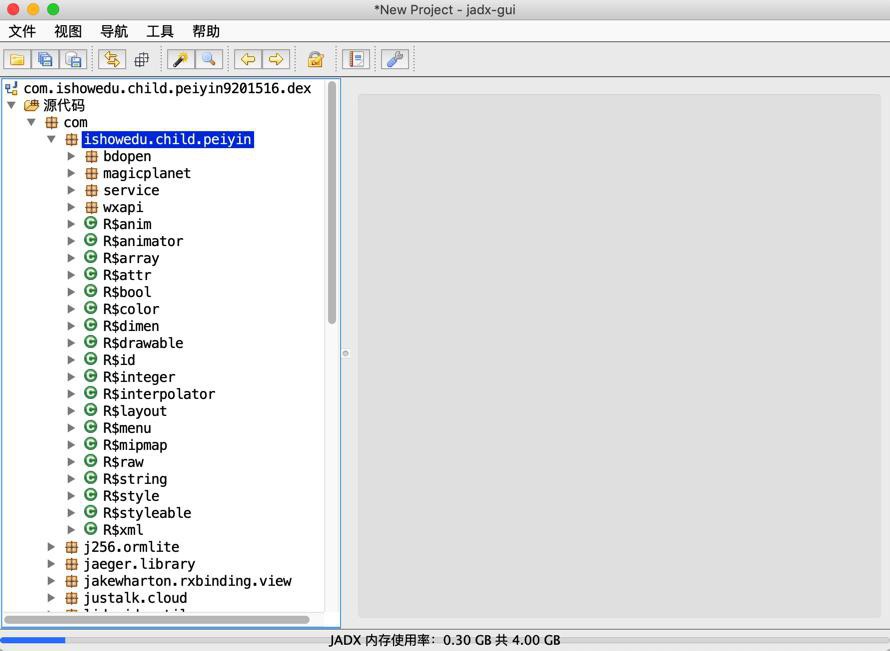
com.ishowedu.child.peiyin9201516.dex:貌似是有comishowedu.child.peiyin的业务逻辑代码的
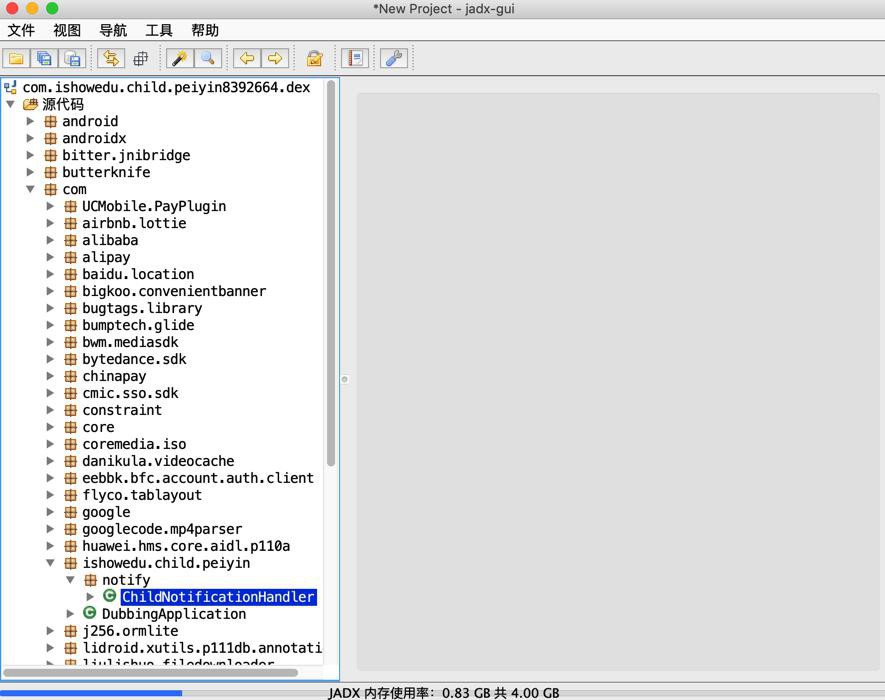
com.ishowedu.child.peiyin8392664.dex
也有一点代码
其他的,看了下,都没有 com.ishowedu.child.peiyin了。
所以就去导出这2个dex为jar
../../../../../reverse_engineering/dex-tools/dex-tools-2.1-SNAPSHOT/d2j-dex2jar.sh -f ../apk_to_dex/com.ishowedu.child.peiyin/com.ishowedu.child.peiyin9201516.dex
输出:
➜ dex_to_jar ll total 15552 -rw------- 1 crifan staff 7.4M 9 16 11:11 com.ishowedu.child.peiyin9201516-dex2jar.jar -rw-r--r-- 1 crifan staff 163K 9 16 11:11 com.ishowedu.child.peiyin9201516-error.zip
以及
../../../../../reverse_engineering/dex-tools/dex-tools-2.1-SNAPSHOT/d2j-dex2jar.sh -f ../apk_to_dex/com.ishowedu.child.peiyin/com.ishowedu.child.peiyin8392664.dex
输出jar:
➜ dex_to_jar ll total 30912 -rw------- 1 crifan staff 7.4M 9 16 11:12 com.ishowedu.child.peiyin8392664-dex2jar.jar -rw-r--r-- 1 crifan staff 103K 9 16 11:12 com.ishowedu.child.peiyin8392664-error.zip -rw------- 1 crifan staff 7.4M 9 16 11:11 com.ishowedu.child.peiyin9201516-dex2jar.jar -rw-r--r-- 1 crifan staff 163K 9 16 11:11 com.ishowedu.child.peiyin9201516-error.zip
注意:
中间也都会输出一些小错误GLITCH和警告WARN
估计内部还是很多细节是无法完美转换的。
再去把jar转java源码
../../../../../reverse_engineering/jadx/jadx-1.0.0/bin/jadx ../dex_to_jar/com.ishowedu.child.peiyin9201516-dex2jar.jar -d .
结果此处报错,转换失败:
➜ jar_to_java ../../../../../reverse_engineering/jadx/jadx-1.0.0/bin/jadx ../dex_to_jar/com.ishowedu.child.peiyin9201516-dex2jar.jar -d . INFO - loading ... INFO - converting to dex: com.ishowedu.child.peiyin9201516-dex2jar.jar ... ERROR - jadx error: Error load file: ../dex_to_jar/com.ishowedu.child.peiyin9201516-dex2jar.jar jadx.core.utils.exceptions.JadxRuntimeException: Error load file: ../dex_to_jar/com.ishowedu.child.peiyin9201516-dex2jar.jar at jadx.api.JadxDecompiler.loadFiles(JadxDecompiler.java:138) at jadx.api.JadxDecompiler.load(JadxDecompiler.java:102) at jadx.cli.JadxCLI.processAndSave(JadxCLI.java:32) at jadx.cli.JadxCLI.main(JadxCLI.java:18) Caused by: jadx.core.utils.exceptions.DecodeException: java class to dex conversion error: dx exception: Translation has been interrupted at jadx.core.utils.files.InputFile.loadFromJar(InputFile.java:191) at jadx.core.utils.files.InputFile.searchDexFiles(InputFile.java:82) at jadx.core.utils.files.InputFile.addFilesFrom(InputFile.java:40) at jadx.api.JadxDecompiler.loadFiles(JadxDecompiler.java:136) ... 3 common frames omitted Caused by: jadx.core.utils.exceptions.JadxException: dx exception: Translation has been interrupted at jadx.core.utils.files.JavaToDex.convert(JavaToDex.java:63) at jadx.core.utils.files.InputFile.loadFromJar(InputFile.java:182) ... 6 common frames omitted Caused by: java.lang.RuntimeException: Translation has been interrupted at com.android.dx.command.dexer.Main.processAllFiles(Main.java:614) at com.android.dx.command.dexer.Main.runMultiDex(Main.java:365) at com.android.dx.command.dexer.Main.runDx(Main.java:286) at jadx.core.utils.files.JavaToDex.convert(JavaToDex.java:49) ... 7 common frames omitted Caused by: java.lang.InterruptedException: Too many errors at com.android.dx.command.dexer.Main.processAllFiles(Main.java:606) ... 10 common frames omitted
结果:
../../../../../reverse_engineering/jadx/jadx-1.0.0/bin/jadx ../dex_to_jar/com.ishowedu.child.peiyin8392664-dex2jar.jar -d .
错误依旧。
算了,直接用jadx-gui去打开dex,然后导出源码吧
文件-》全部保存
导出后的代码
VSCode去打开
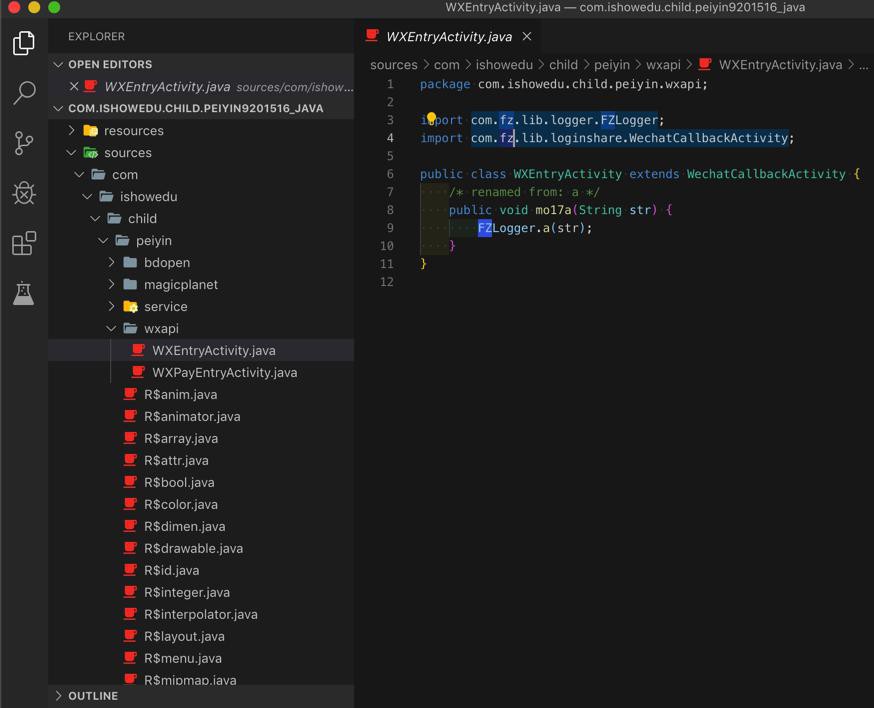
发现还缺少(之前看代码而直到的)fz的库
所以还要去找到之前哪个dex包含com.fz的库
找到了
com.ishowedu.child.peiyin8392664.dex
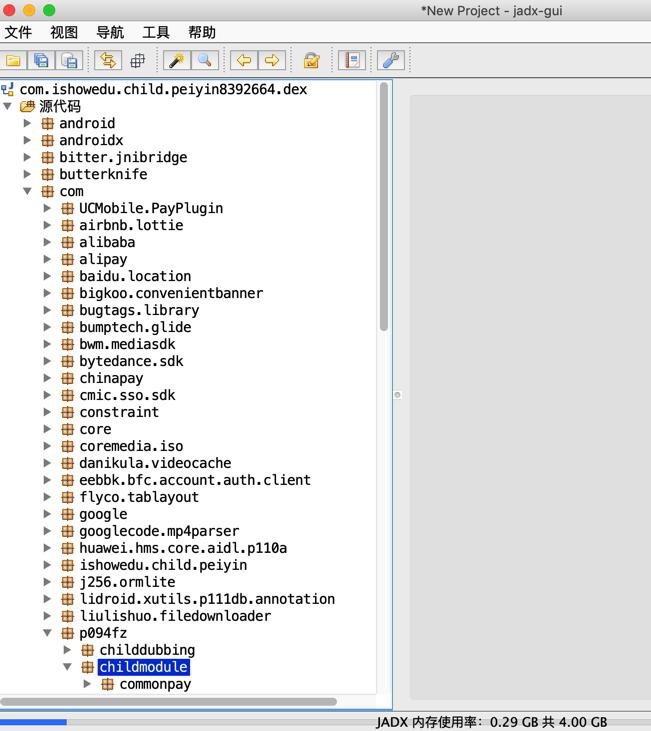
是有fz的,但是不是完美的解码出fz,而是
p094fz
其下有我们希望看到的childmodule
(manifest.xml中有很多childmodule子模块)
以及:
下面有我们希望的
FZNetManager
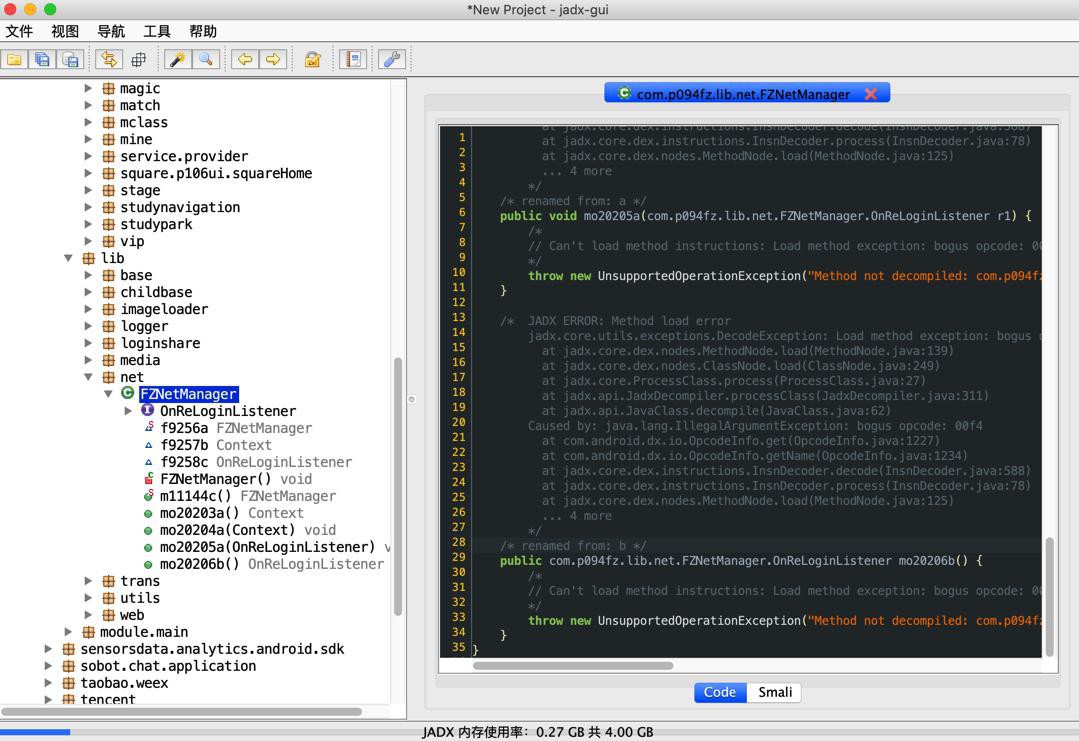
但是尴尬的是
解码失败了
/* renamed from: a */
public void mo20205a(com.p094fz.lib.net.FZNetManager.OnReLoginListener r1) {
/*
// Can't load method instructions: Load method exception: bogus opcode: 00f7 in method: com.fz.lib.net.FZNetManager.a(com.fz.lib.net.FZNetManager$OnReLoginListener):void, dex: com.ishowedu.child.peiyin8392664.dex
*/
throw new UnsupportedOperationException("Method not decompiled: com.p094fz.lib.net.FZNetManager.mo20205a(com.fz.lib.net.FZNetManager$OnReLoginListener):void");
}看不到真正源码
那还是去jadx的cli命令行去试试
从dex转java,看看能否转出源码,源码是否可读
../../../../../../reverse_engineering/jadx/jadx-1.0.0/bin/jadx ../../apk_to_dex/com.ishowedu.child.peiyin/com.ishowedu.child.peiyin8392664.dex -d com.ishowedu.child.peiyin8392664_java
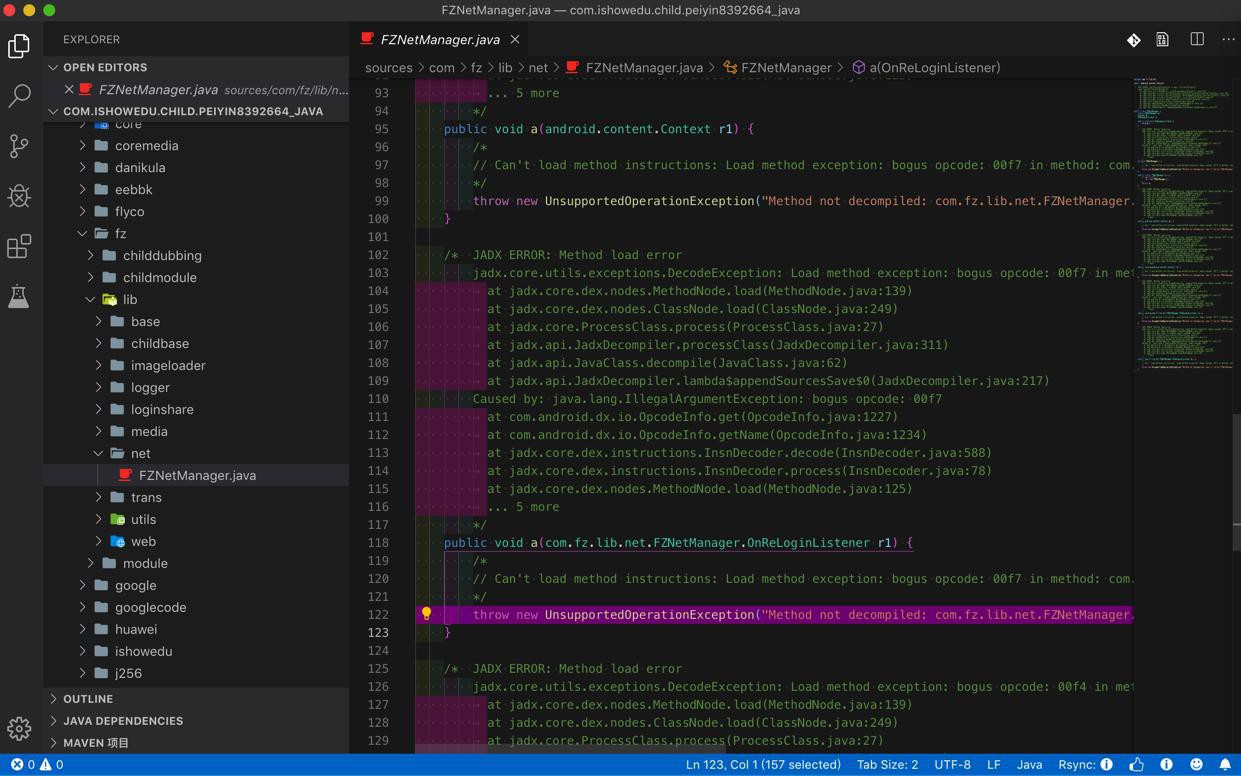
可以转换,但是最关键的
sources/com/fz/lib/net/FZNetManager.java
中的函数都转换出错,看不到源码:
那另外去试试,Procyon把dex转jar,看看转换效果
参考
和自己之前的:
【已解决】用基于Procyon的Luyten反编译安卓jar包得到java源码
【已解决】用Procyon命令行去从jar包导出java源代码
去下载更新版本的
然后去运行:
java -jar /Users/crifan/dev/dev_tool/android/reverse_engineering/Procyon/procyon-decompiler-0.5.36.jar -jar ../../dex_to_jar/com.ishowedu.child.peiyin8392664-dex2jar.jar -o com.ishowedu.child.peiyin8392664_java
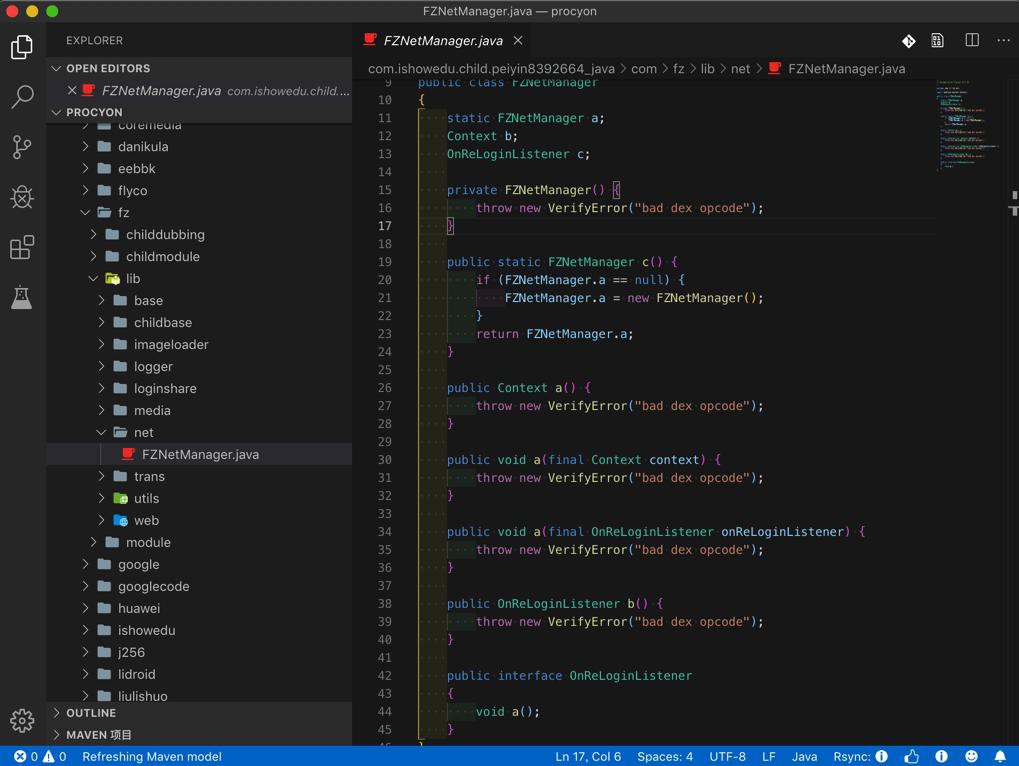
结果类似:可以转换,但是核心代码
com.ishowedu.child.peiyin8392664_java/com/fz/lib/net/FZNetManager.java
出错看不到源码
【总结】
此处结论已整理至: